Authoritarianism, Globalism, and my gadget shipments
OK, I have a problem. I’ll admit it. I order gadgets and components from Aliexpress. And then they arrive some random time in the future (1 week to 3 months!). And usually the sellers give you a quick email “your thing is on the way, give me good feedback please, shipping speed is not in…
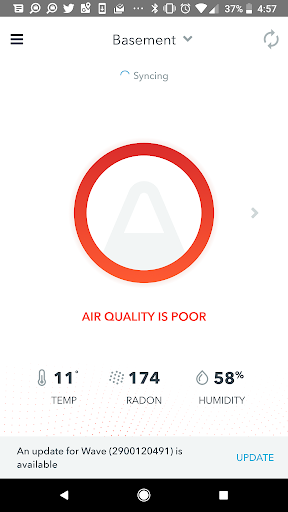
What, more Radon in the Waterloo Ontario region?
Another reader has purchased the gadget and found an issue. If you still think “this couldn’t happen to me, my dank wet basement is in a Radon-free zone, well, you are only right in the sense the Radon is free. Free to invade your lungs, cause lung cancer. If you are still trying to convince…
2018 upcoming CVE’s, sneak peak, courtesy xkcd
I have to believe this is entirely true.
Wireguard: simple VPN/tunnels
For a while now I have been intrigued by Wireguard. Its kind of like a cross between ssh and ipsec. You can create a point-to-point link very easily, and the authentication is public-key based (like SSH). The host gets a new Ethernet interface, and that is your tunnel. Beauty! I think this could be a…
My laptop got insomnia: Secureboot and the mobile machine. Hibernate is the collateral damage
So a funny confluence of events has happened in my life. Until recently the majority of my time was spent with a mobile machine, so it got used every day. When I wasn’t using it, it slept in S3 state (suspend to ram). Since I used it every day, it never ran out of battery…

Long Strange Trip