
learninghacking, I visited Canada Computers today to see what ‘extended boxing week sale’ they had. And lo and behold, it was this. A Trendnet WiFi HD Baby Cam TV-IP745SIC. $19. Sweet. Since this is designed to be in your home, monitoring your baby, with bidirectional audio, and cloud access, they must have taken pains to secure it right? They go to great pains to explain ‘designed in USA’ so one cannot use the convenient ‘but insecure consumer gadget china…’ argument if not.
It arrived with firmware 1.0.0 (always ominous!), dated 2014/1/ 03:32:55, build number 4521.
(The conclusions are at the end, hint: the cloud has no security, buy this if you want random people to see, hear, and talk to your kids while you are not around).
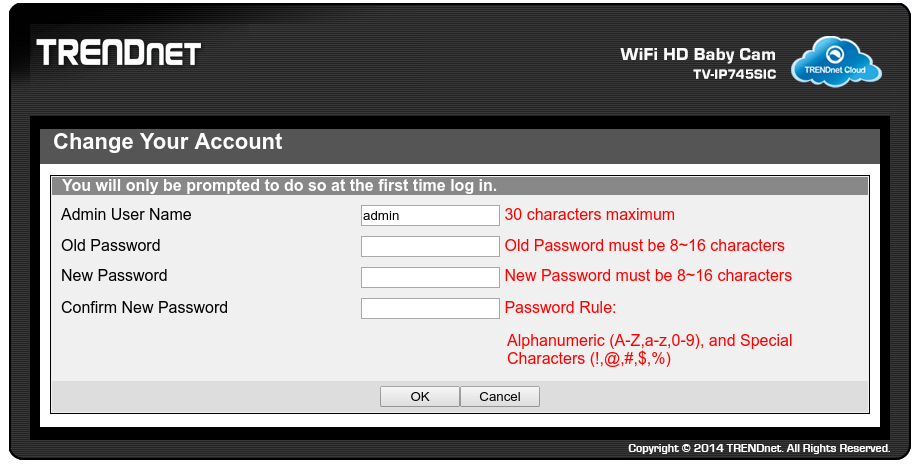
Presented with a forced-change of password, which must be 8-16 characters, I chose admin123 (7 characters), and it worked. Hmm.
It appears a plugin is required. As you might expect, the link is to a Windows MSI file (stored on the device).
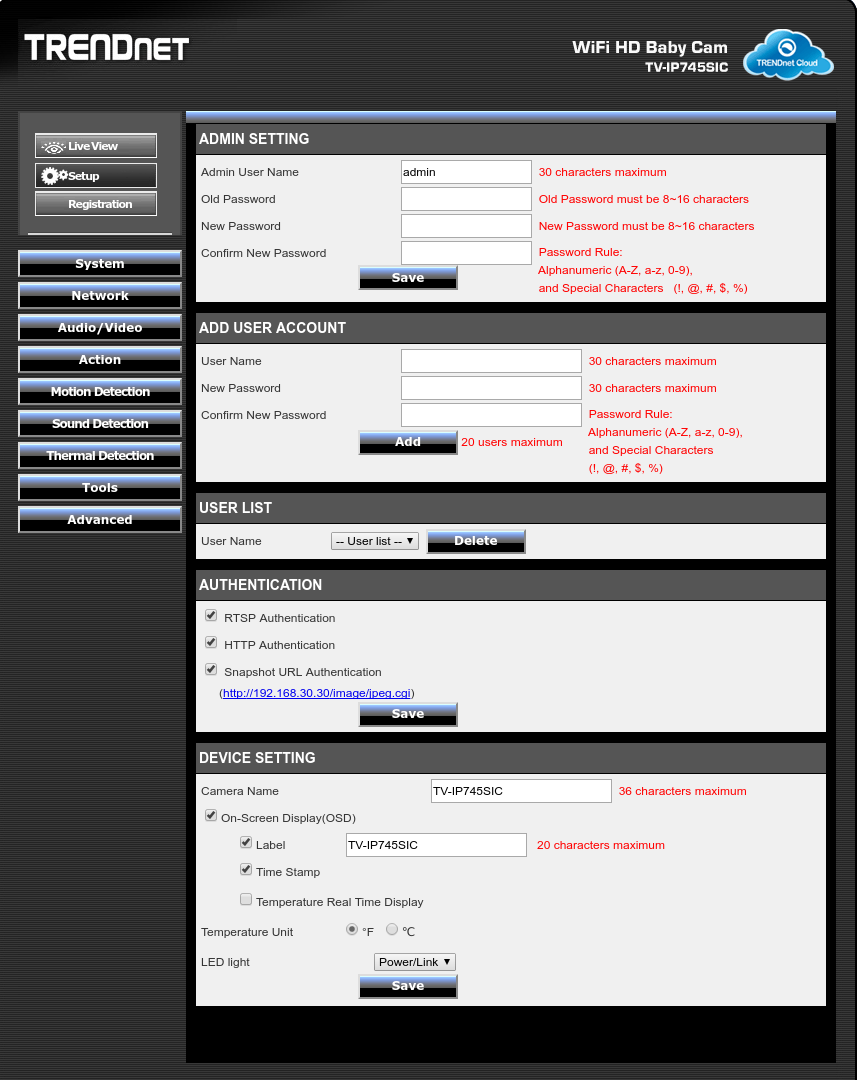
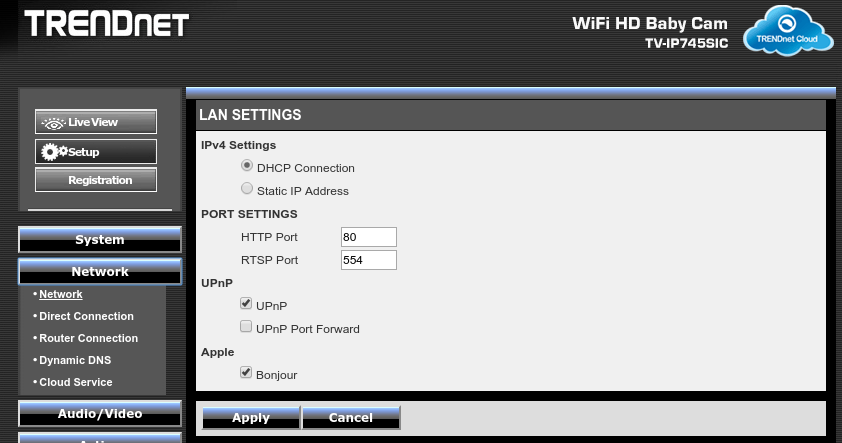
Now the attempt at security is, although not exactly life-support-on-space-mission strong, still reasonable for a home device that is not internet-facing. By default it requires auth on http/rtsp/snapshots.
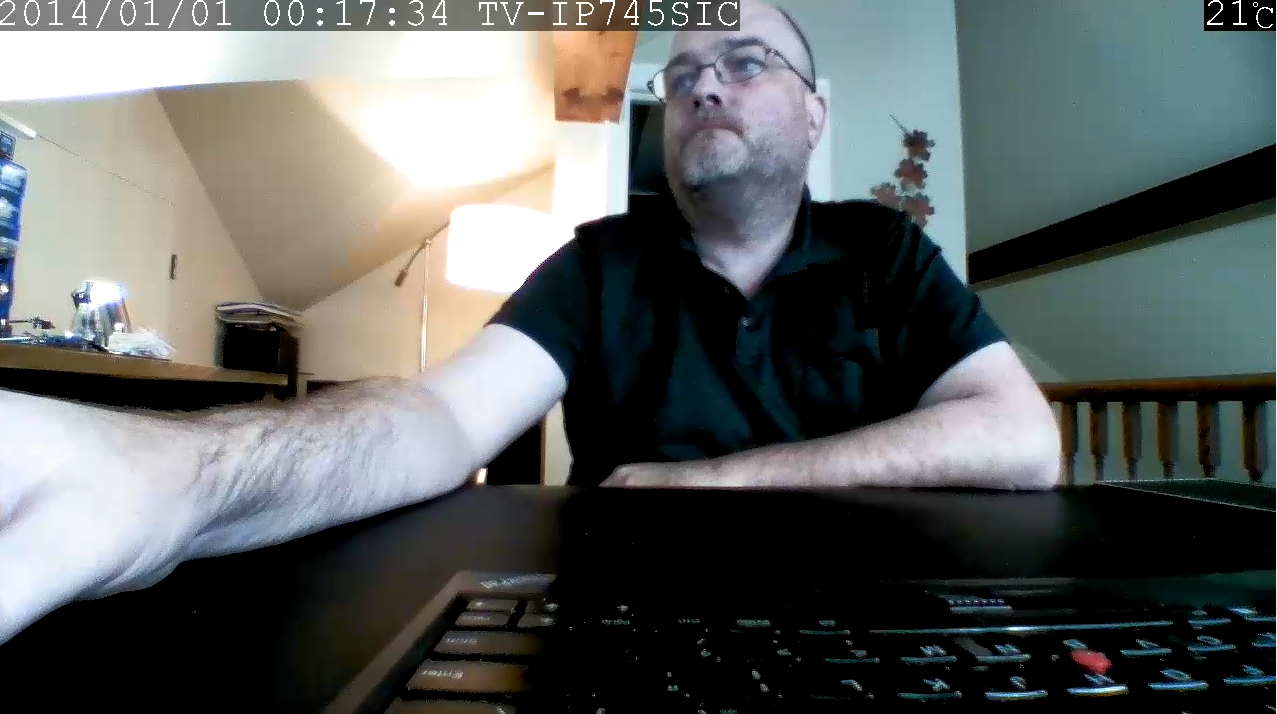
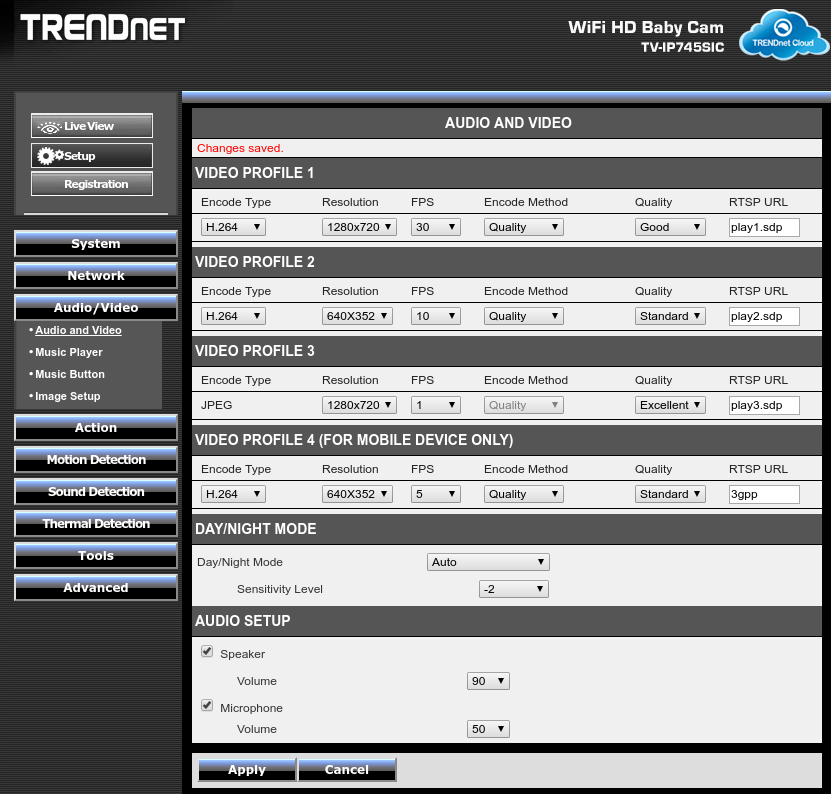
If we open vlc to it (vlc rtsp://192.168.30.30/play1.sdp), we get live video, with the *highest* quality of lens! We can also get a jpeg snapshot from http://192.168.30.30/image/jpeg.cgi.
If we hit the ‘play/pause’ button on the top, it starts to play some music-box-dancer piano song. Nice.
The default UPnP setup is enabled for discovery, but not opening the firewall. So far so good.
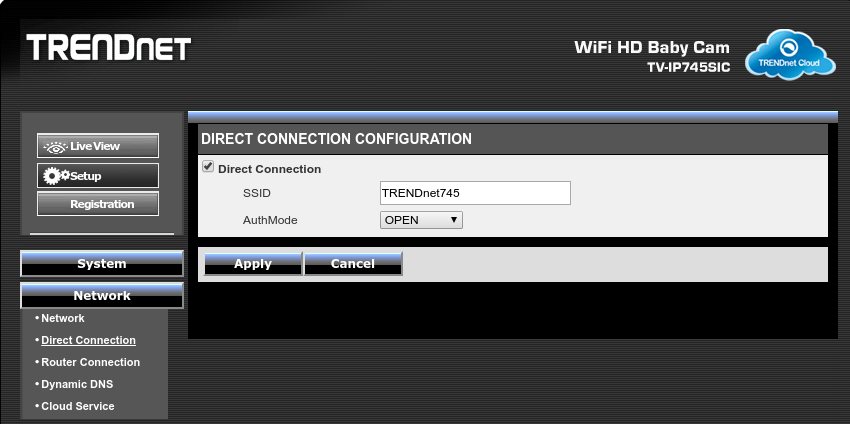
The default WiFi is direct, enabled, no auth, not too happy about that:
The device has a mode where it can save video to an SD card. And it conveniently will serve those files over its web interface for you.
It has sound detection, so you can cause an alert when something occurs (as well as motion and temperature).
Interestingly it has 4 profiles for RTSP, about 3 more than I figured it would have.
OK, enough looking at it in the ‘no internet mode’, time to do some captures and let it loose on the world. It gives me a URL (http://85945000.cam.trendnetcloud.com/), which is *my* cloud URL for it. As soon as the device hits the internet, this becomes live. Sadly:
Browser Compatibility Notice
The browser version you are using (Google Chrome 63.0.3239.84) is not supported by the TRENDnet Cloud service. If you are using a mobile device, please download the TRENDnet CloudVIEW mobile app. You can also use one of the following browsers on your computer to view your camera:
Internet Explorer (Windows desktop version only): IE9.0 to IE11.0
Safari (Mac version only): 5.1.7
Firefox: version 22.0 to 37.0
Google Chrome (Windows desktop version only): version 28.0 to 40.0
GET /users/stream_info.cgi HTTP/1.1 Host: 10.255.254.94 Referer: http://10.255.254.94:80/users/stream_info.cgi User-Agent: Mozilla/4.0 (compatible; MSIE 5.5; Windows NT 5.0) HTTP/1.1 401 Unauthorized WWW-Authenticate: Digest realm="nipca", nonce="9261151863c4390bb053da7f837a6790c20010ac", qop="auth" Content-Type: text/html Content-Length: 91 Date: Sat, 30 Dec 2017 20:47:26 GMT Server: dcs-lig-httpd Unauthorized Please enter correct account/password. GET /users/stream_info.cgi HTTP/1.1 Host: 10.255.254.94 Referer: http://10.255.254.94:80/users/stream_info.cgi User-Agent: Mozilla/4.0 (compatible; MSIE 5.5; Windows NT 5.0) Authorization: Digest username="admin", realm="nipca", qop="auth", algorithm="MD5", uri="/users/stream_info.cgi", nonce="9261151863c4390bb053da7f837a6790c20010ac", nc=00000001, cnonce="ad9d46c392d98dc66a33d083ec62b770", response="fa5c5c9fe59c8787cc74a35c2c883099" HTTP/1.1 200 OK ...
OK, so what did we learn?
An attempt was made to secure the device locally. If it had no internet access, this would have been in the realm of ‘normal’ for such consumer devices.
The cloud interface is not secure. It makes no particular attempt.
The cloud interface bypasses your firewall. Without even using the port-forwarding. The device connects outbound, and allows things inbound on this, bridged in their cloud app.
No encryption is used, and hard-coded credentials.
Conclusion: buy this if you want random people to be able to see, hear, and talk, to your kids when you are not around. $20 well spent.

Leave a Reply to Jayme Snyder Cancel reply