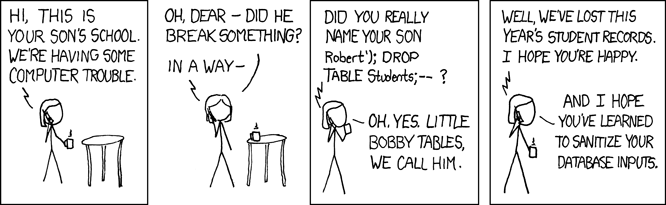
Bobby Tables Meets Password Breach
We’ve all seen the “Little Bobby Tables” comic, explaining the perils of unsanitised input, SQL injection. Now, what if we were to turn the tables on attackers with this exact method? Maybe make your password be something with a comma, so all the CSV dumps that are bought and sold break?
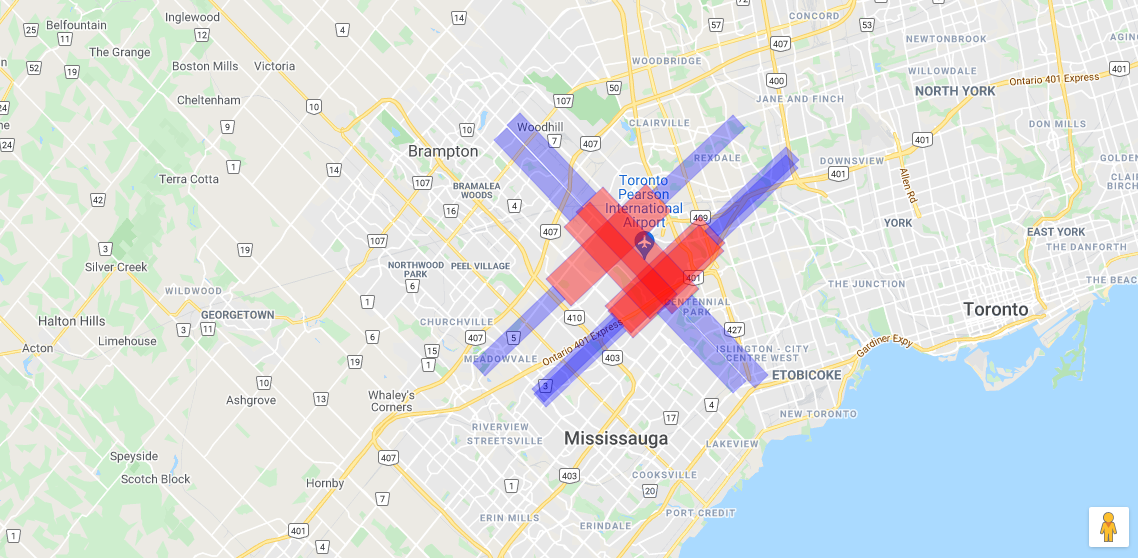
Self Driving Cars and Airport Proximity
5G exclusion zones announced around airports. Self-driving cars take note!
You know your brake pads are done when…
You know your brakes are shot when there’s nothing but squeak and you can read the stamp on the backing pad…
Bike Upgrade: The Bike Gets an Elevator
Bike seat too tall to get on? and too low to ride? Install an elevator!
My Sam Knows Results
My initial Sam Knows results (for my second generation of tests): its quite consistent.

Long Strange Trip