Author: db
The Web Is Not An Executable
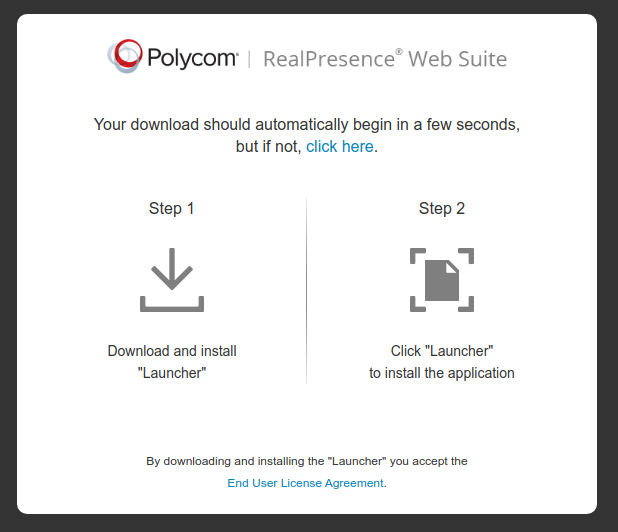
Its 2021. By this stage everything has a browser in it. Imagine my surprise, invited to be part of an upcoming online web event, and, this is the experience. It even says ‘Web Suite’ in the name. Nonetheless, it auto-downloads a Windows executable.
Back on the Sam Knows Bandwagon
Back on the sam knows benchmarking the internet bandwagon. The whitebox arrives.
Zen and the Art of Motorcycle Maintenance
As a young lad my father’s prize possession was a BMW R69S motorcycle (’67 or ’68 year). Years passed, I came on the scene, the bike became a thing which was polished rather than ridden, and then a thing in the drive shed that was ignored.
1947-2021: RIP old man
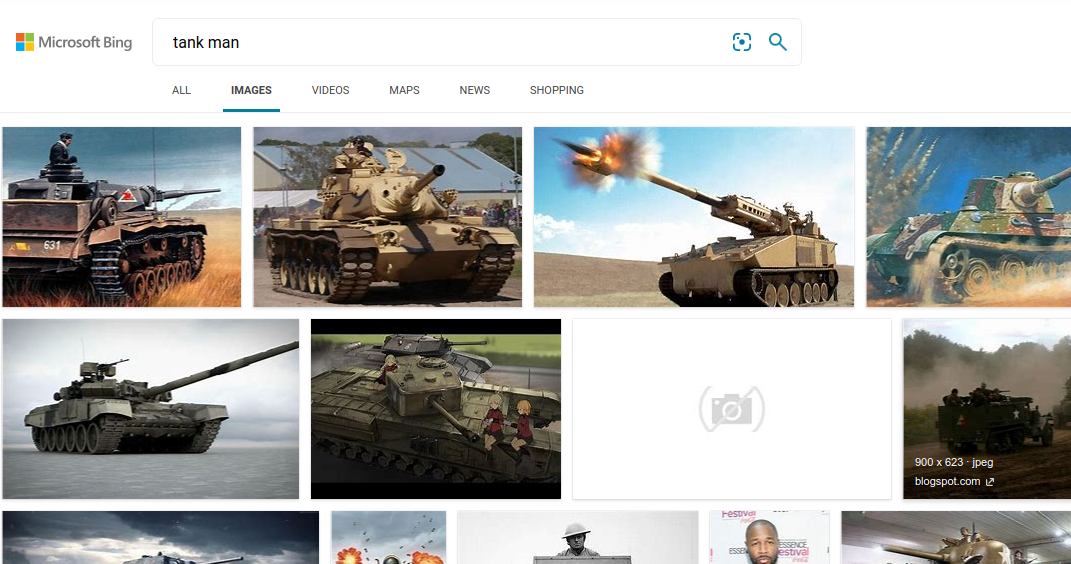
Shame on Microsoft
Microsoft Bing censoring Tiananmen square searches.