Month: February 2018
Cryptokitty: collectable, breedable, adorable. This is meow life now
https://www.cryptokitties.co/. You buy a virtual cat with virtual currency. And then, unlike regular cats, you pay to get them knocked up and have kittens. But its ok, its with virtual currency. Is this the end-goal of the ‘I own nothing’ world we are entering, where uber + self-driving cars instead of owning, airbnb instead of…
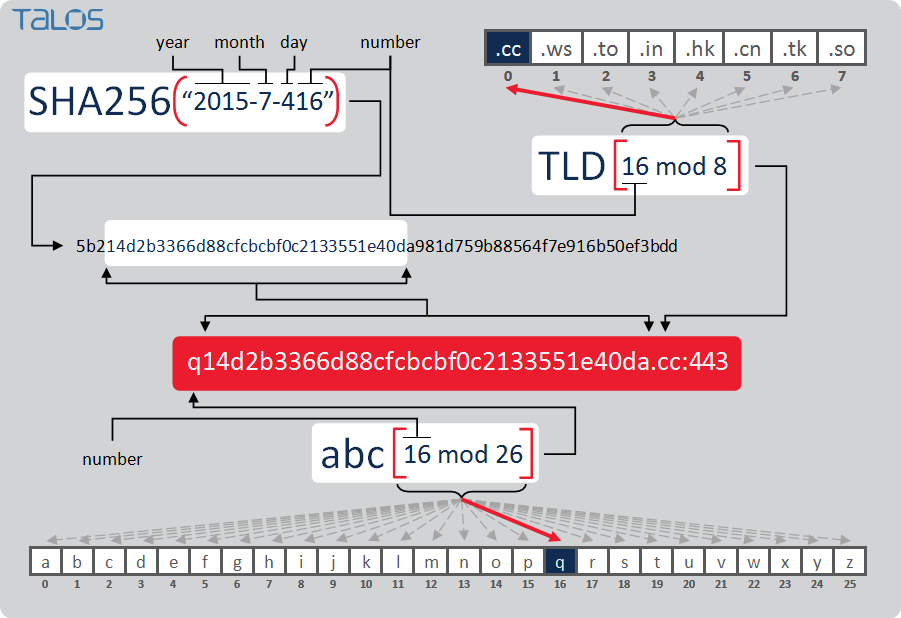
Machine Learning as a way to block ads (that carry malware? specifically crypto-miners)
OK, fess up. Most of you run adblock(plus/adaware/pihole/…). And you love it. Other than Forbes, the world is a kinder gentler place. But recently some of you may have noticed the battery on your laptop is poor, your fans run more. You are a victim of drive-by crypto-mining (probably monero, but could be bitcoin or…
vermut: first time in 10 years w/o
First time in 10 years w/o for me. Have fun all!
Is my password known? A problem
So everyday there is a new site which fesses up that they have been pwned. Someone came in, stole the lot, but don’t worry, they only got something minor. And then a few days later, well, it seems there was a bit more. And by the time you stop caring about the story, it comes…
Security liability for software vendors, open source on end of support? Great ideas France!
This is a tough slog of a read (167 pages), but there is a proposal from France on cyber security (the parent web page here). I tried a machine-translation to English, but, well, the fonts are embedded as images somehow. Hmm, its like a scan, its a set of pictures. Boo. OCR? What is this,…