Many bots exist which scan your repo’s and send you automatic pull requests when some library you use has become vulnerable. Its a good service: it generates a lot of noise, but is better than the alternative of continuing w/ the vulnerable upstream.
Usually I just eyeball, click accept, and go. Its key to do that eyeball, who knows when someone will have a bot that tries to get you to accept bad sw in a PR!
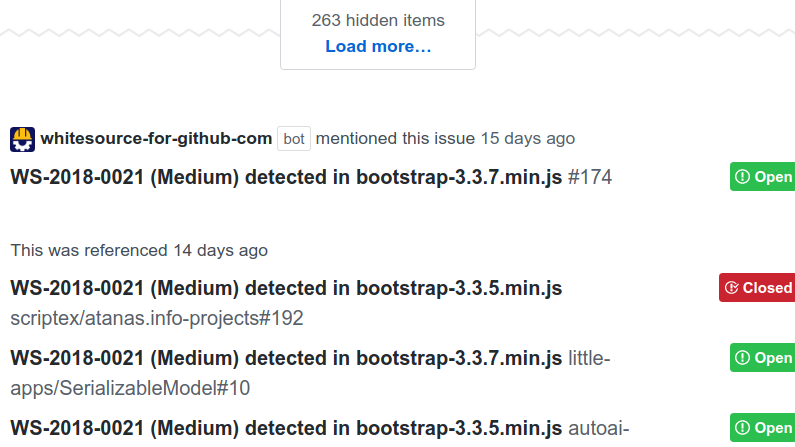
Today I was looking at a vulnerability in Bootstrap, and XSS attack. And, at the bottom, github has helpfully showing all the PR that mention this issue. E.g. the dictionary of all the vulnerable software.
Let’s say I’m a lazy attacker. I come into possession of a single exploit. I just watch the issue, and, whenever new sw is appended, I attack it.
I’m not suggesting any change here. A less lazy attacker could scan github themself. The bots are better than the alternative of the bad software getting put in the package requirements and forgotten. Merely musing, it doesn’t take much to find low hanging vulnerabilities.
What’s sadder, some folks are using decade old vulnerabilities. Bootstrap 2.1.0 was released in 2012, its in the list here. Now, some of these might be dead-forks (e.g. people fork something on github and then let their fork die). This one for example. This is why its important to only use open source from the source, curated, lively, active.
Why was I rearching XSS in Bootstrap? It was for my new feature-length thriller movie, below. Side note: I might have to relocate the recording studio, my downstairs neighbours AC runs through it, and, despite audacity noise reduction filter, comes through. Boo.
I talk a bit more about this on my corporate blog.
Leave a Reply