Month: November 2018
Supply chain risk: more javascript npm shenanigans, OSS governance
Lately I’ve been talking a lot about the supply chain risk. You import some software, and are suddenly importing their business model and practices. Well, we’ve just had another ‘shenanigan’ unveiled. And its got some good drama. https://github.com/dominictarr/event-stream/issues/116 In a nutshell there is some package which is relatively stable. The original developer doesn’t use it anymore,…
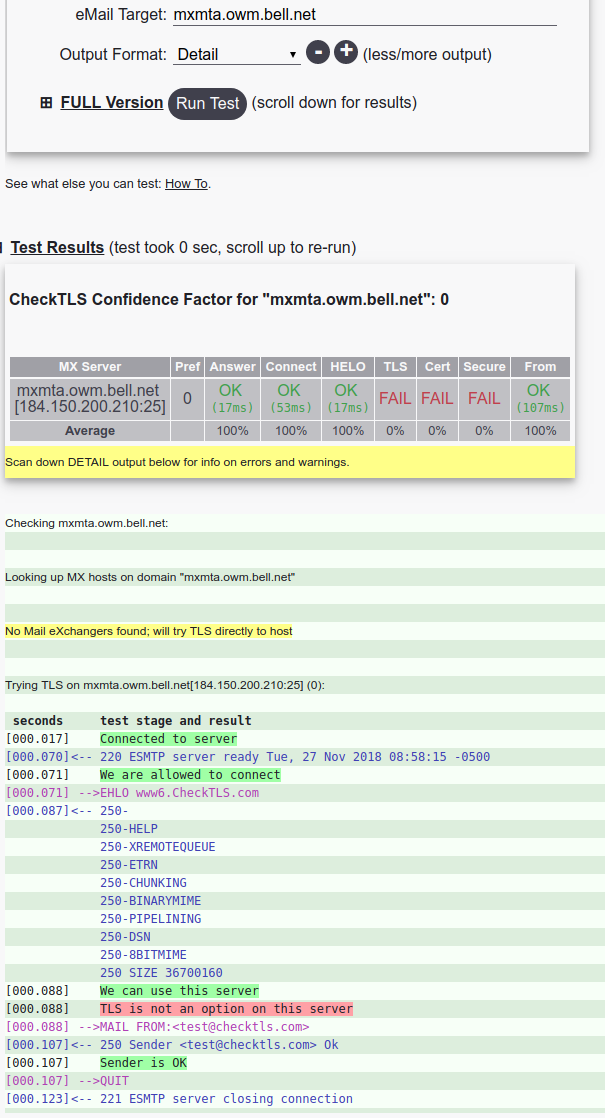
Why does Bell Canada not allow encrypting your email in transit?
Hint: you want your email to be encrypted in transit. Now, lets take a look at some stats. From my earlier post about ‘Why is Canada less encrypted than the US‘?, and from Google’s Transparency Report, we dig into Sympatico. This is Bell Canada‘s brand for Internet. We see that there is no encrypted email exchanged…
Do the phish scammers care more about your security than you do?
Phishing has hit the halfway point on encryption. This means that being TLS-encrypted is no indication a site is real or not (its an indication that it is exactly what it says it is, but not what it might appear as). Ironically, they might be stronger than the average web site. If we look at…
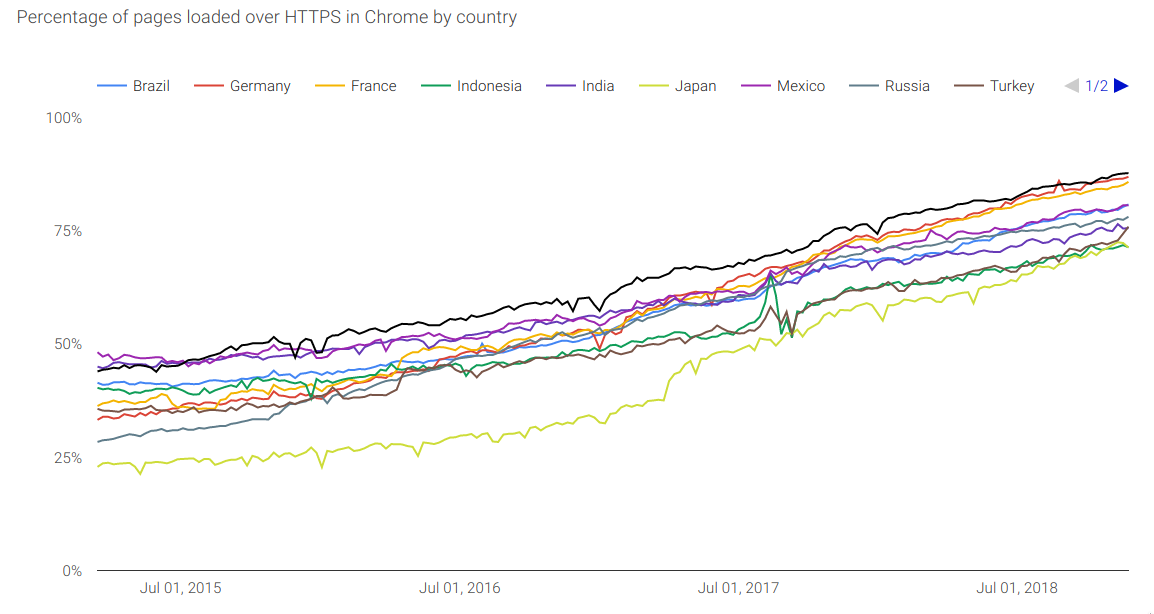
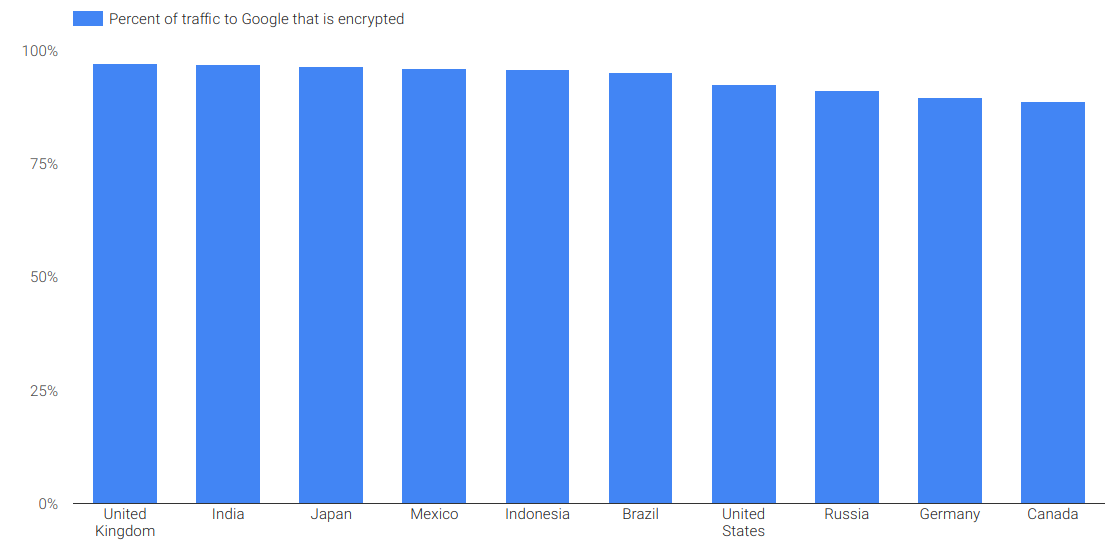
Why is Canada worse than the UK and US for encrypted web?
Courtesy of our friends @ Google and their Transparency Report we see that Canada is 89% encrypted to Google. Good, but not great when you realise the UK is 97% encrypted. What could drive this difference? I would think device-types and ages would be similar. This traffic is a bellwether of other encrypted traffic, and we…
Next Chautauqua: Continuous Integration!
Tomorrow (Tues 27, 2018) we’re going to have the next meetup to talk Continuous Integration. Got a burning desire to rant about the flakiness of an infinite number of shell scripts bundled into a container and shipped to a remote agent that is more or less busy at different hours? Wondering if its better to use…