You’ve by now seen the most recent Bloomberg article that suggests a “major US telecom” has equipment (again made by SuperMicro) with modifications, this time to the Ethernet. Is this plausible? [I have no information on the story or if it occurred, I’m merely discussing the plausibility].
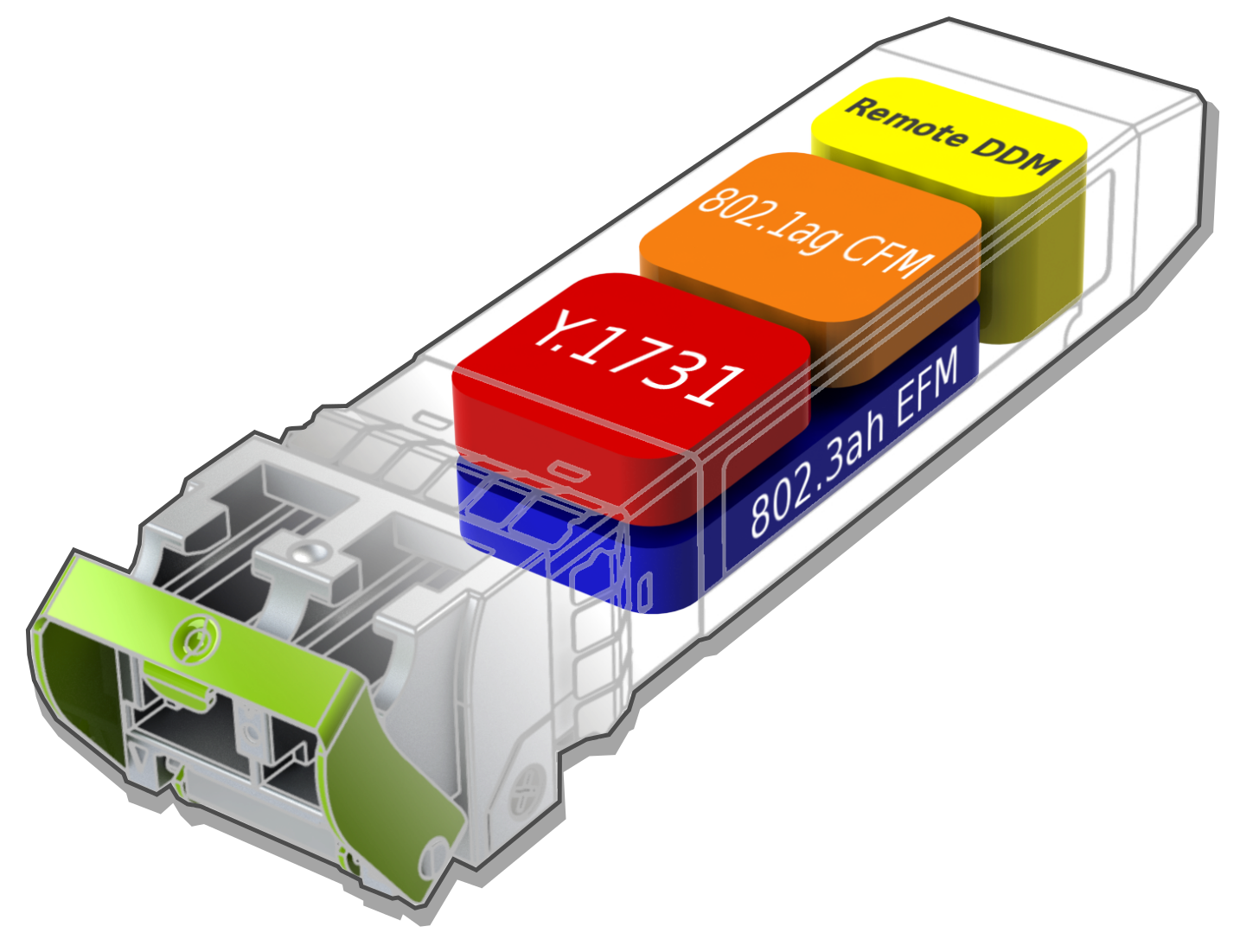
In a word, yes. First, although the image shows copper (RJ45 connector), many telecom servers are wired using fibre. So lets take a look at a ‘smart SFP‘. What’s an SFP you ask? Its a ‘Small Form-Factor Pluggable Transceiver‘. In a word, its your Ethernet jack. And there are indeed companies who make very small hardware that go inside them that allows capturing traffic and sending it to a remote site (or injecting traffic).
You can see some more information on a type of smart SFP by looking at the Rad MiNID. And there are other manufacturers out there, e.g. Viavi (JDSU).
So hypothetically someone wandered into a room full of telecom servers, they could insert one of this smart SFP and it would be not easily spotted. That smart SFP could indeed capture and/or interact with traffic, locally in that room, from far away.
Now, if the interface were indeed copper, its a bit trickier. Adding a second set of transceiver logic, a bridge, etc., that would take more real-estate. Doable I guess. A device like this ‘packet squirrel‘ could also be used.
Leave a Reply to Jayme Snyder Cancel reply