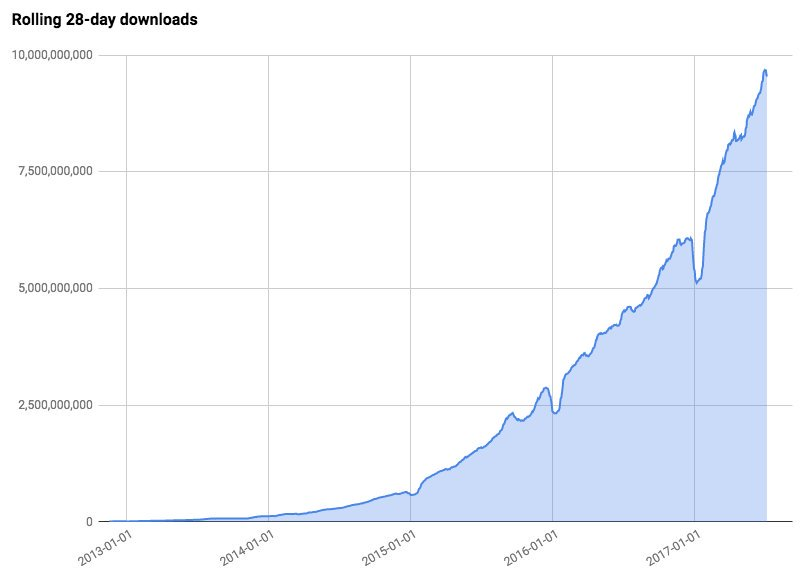
npm (the nodejs aka Javascript package manager) has ~10B packages downloaded in a rolling 28-day period [source: Laurie Voss]. So clearly there is no person looking at each download. And, npm is unsigned. So, well, each download could be different, even if its of the ‘same’ file.
We’ve had some incidents where npm packages were ‘absconded with’. E.g. where they vanished, or became something else. Famously, Kik (the instant-messenger) sent a take-down notice to a developer because of the ‘kik’ module he wrote. And then took over the packages on the npm system without his permission. And this instantly broke a ton of web sites and apps. In fact, there were 2.5M downloads (uses) of the package in the trailing month.
Recently we saw British Airways, NewEgg (and others) become hacked on their web sites via Javascript injection. Using a technique much like this one. (people sometimes ‘typo-squat’, e.g. register a similar-named package which is initially functional and not malicious, and later change it). There are also ‘zombie’ projects, where the developer loses control or goes away, and someone swoops in.
Now, with ~10B downloads, of unsigned packages, from random developers who may or may not have 100% control of their code, their delivery process, due to internal and external causes, we clearly have a critical risk. How could we solve this?
Well, signing the world… not gonna happen.
- People ignore the signing errors
- Its hard to securely sign things
- The above kik issue, they could have just signed a new copy
- Expense, cost, …
So, what alternatives do we have absent a run on the tin-foil supply for toques? Well what about some sort of ‘web-of-trust’. E.g. every time I download a package, I hash the contents and publish an assertion I am using it. You, depending on your risk tolerate, look to what the ‘score’ is of how many people trust it. If you are a bank, you set it to high, if you are less fussed, you set it to low. Trust might also be how long its been unchanged, number of distinct apps using it, etc.
Now, I hear you say, who would publish their bill-of-materials of what they are using from upstream? Open source does, but what about other things? Can we use blockchain to solve this you ask?
Well of course you can. Blockchain solves all! We can use a ring-signature technique (similar to what is used in Monero), this allows people to publish to the ring privately. You know that only a member could publish this fact, but not which member. Its sort of like the 6-member firing squad with all but one gun having blanks, you know the group which was involved, but not the individual.
We also have the issue of notification and revocation. Lets assume that 2.5M of us have used that trim left whitespace kik code. All of a sudden the repo is replaced. One of us finds it, how do we notify the others? In the certificate world there is the CRL (certificate revocation list), we could publish a similar de-assertion to the list.
Anyone else have any suggestions? It seems this is a widely known and exploited issue with no clear solution in sight.
Leave a Reply