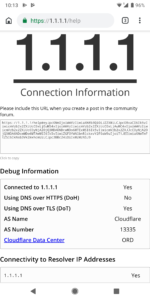
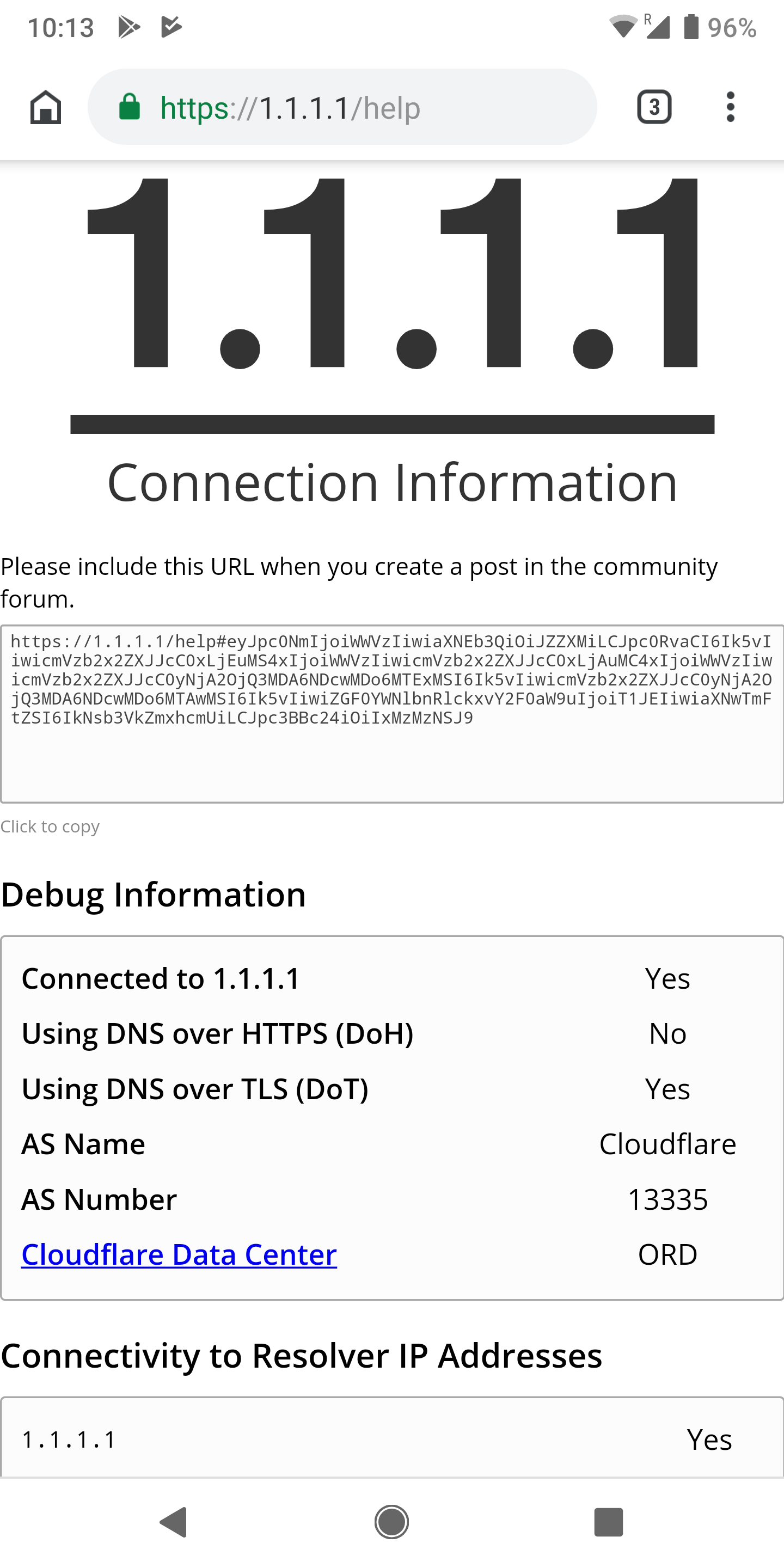
In Android Pie private dns is a feature, in automatic mode by default. This means the default mode of current android is to use encrypted dns to google. But, what if u want to use 1.1.1.1 from cloudflare? They don’t log or snoop your data.
well, here you go. That was easy. Your privacy and security just went way up. good job, take the rest of the morning off.
Note: since automatic is the default, a lot of things will change as this feature rolls out.
Leave a Reply to db Cancel reply