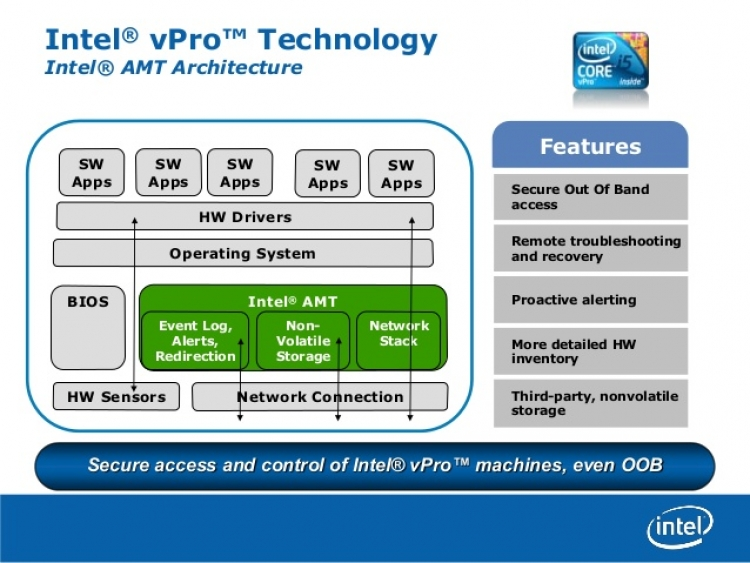
Well this is awkward. That Intel Management Engine (AMT) that you can’t disable. That one that runs even when your machine is turned off. The one that runs with highest privilege, no oversight, outside your operating system. The same one that everyone wonders, just what is in there.
Turns out, from the security audit, some not so great flaws. And the upshot is if you are running an older processor (3rd generation into core or later) it would be a good time to discard it.
If its 4th gen Intel core or later you own, you can consider getting a firmware update from the vendor of your motherboard.
You can find out your generation of processor, and whether it has AMT (vPro, ME) from ark.intel.com.
Now, if we apply our secret decoder ring to the CVSSv3 Vectors:
CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
Hmm. Attack Vector: Network, Adjacent. Privilege required: none, user interaction: none.
So this means anyone who can get onto the same subnet as you (or a remote subnet if you route) can own your machine. This includes from itself, meaning unprivileged local code can escalate up.
If I snoop around my house, I still have two systems in operation that are:
- vulnerable
- no fix
My i7-3770s NAS is the complex one. Its doing what i want and i don’t really want to swap it out. Hmm.
Leave a Reply