Say it ain’t so, etcd is on the public Internets? And its leaking like a sieve.
A Shodan query shows 2593 etcd services out there flapping in the breeze. More detail was covered in Giovanni Collazo blog, but, in a nutshell, the combination of:
- simplicity. Its just easy to use and deploy etcd
- Insecure by design and default. To make it simple, no security model was originally used, if you can access the port, you can read the world
- orchestration platforms using etcd to move config around, including the link between container A and container B (e.g. mysql-client and mysql-server).
is super-dangerous.
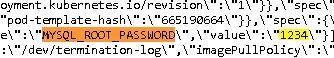
In the tweet about this, we see a great screen shot, mysql password is 1234. Yup. The same one that Spaceballs talked about.
You can’t ‘yada yada yada’ cloud security. You need a real firewall, particularly when you are playing with ‘this only works on a dedicated network that is isolated even from the rest of your own application stack’ stuff like etcd. Seriously, you can’t even just be ‘outside bad, inside good’, you need to think about lateral traversal. if one machine of yours is compromised, and it can walk around in etcd (maybe it changes that password? just reads it? Its bad regardless). And its probably hard to retool everything.


Leave a Reply