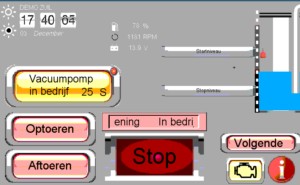
This is part of some factory automation. Perhaps it runs one of the famous pumping systems that keeps the Netherlands from going underwater? Perhaps on the Zuiderzee? Probably not, but, its not inconceivable that hitting that STOP button will have bad affects for people. And, no password, standard port, no firewall (not even NAT, which, although not a firewall despite what these guys say, would at least hide the port by default).
Some are just wide open machines, ready to open the browser (and someone has in this example. Yes you can open this machine and browse to your hearts content). Could this become a untraceable trail for criminal activity? Could the owner of the site be surprised by various subpoena and police visits as a result?
They’ve left their browser logged in to various services, I wonder if they will like bad things on Facebook? Or worse? Perhaps their amazon account is logged in and they order a few hundred Kg of microwave Chicharrones? The cheap kind w/ bits of hair left in it and the tattoo still on?
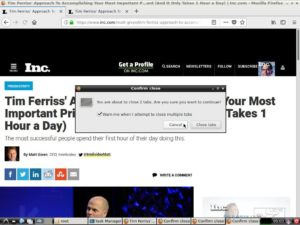
Or installs a keylogger and drains their account? Its really hard to imagine this is the desired state of their computer.
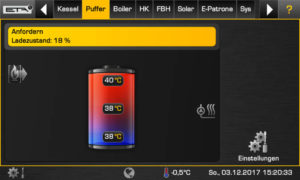
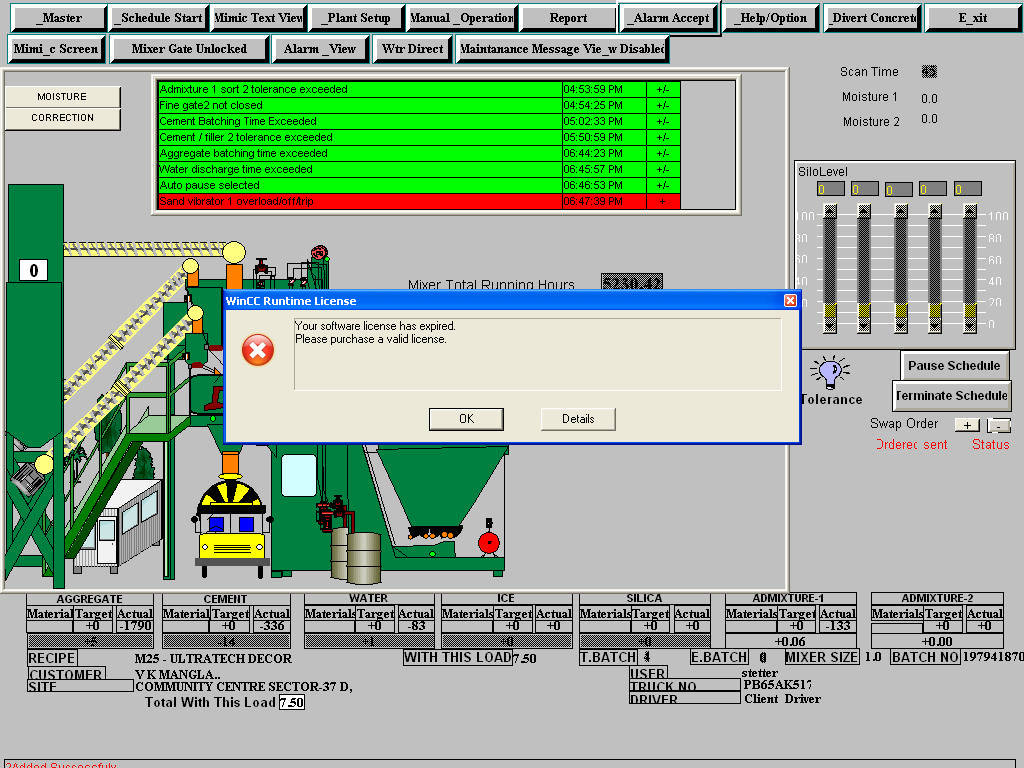
Continuining with the theme of industrial automation gone wrong, what about this company? They are running a SCADA HMI (human-machine-interface) from Siemens called WinCC. And they might be in arrears on their license 🙂
Now, aside from the stunning up-to-date beauty of this modern user interface, can you imagine any trouble in this concrete mixing system? I mean, we can correct for moisture, change the mix. We can turn on/off the flow of concrete. Think of the trouble we could cause, we could make weak concrete that later didn’t hold up and buildings would fail. We could dump concrete when there is no truck to accept it and damage the plant. Its really hard for me to imagine that the owner of this system would be excited to know that the great unwashed (that is you) are one click away from finding it in a public search engine.
So what is the solution? Enable some sort of incentive system to that Internet white-hats hunt and inform? But how would you inform these people? Auto-firewall? Poison Shodan so it has a bunch of fake entries and reduce its usefulness so that only more determined folks can find? Fine the culprits? Despair? Hand-Wringing?
Leave a Reply to Kevin Cancel reply