Month: December 2017
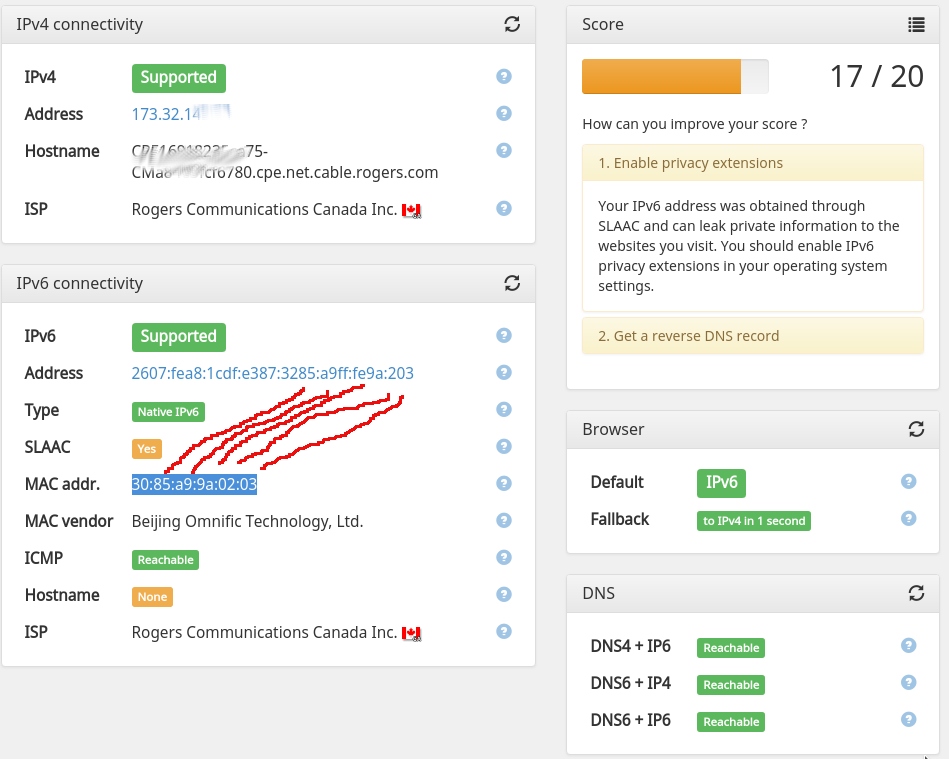
Slaac’ing off on ipv6 privacy
IPv6. Yes its a thing, yes you want it, etc. But did you know it can add more tracking footprint to an already highly trackable world? IPv6 is commonly allocated within a home environment using a protocol called SLAAC (stateless local address auto configuration). Its sort of a fancy way of picking an IP address…
What are we buying? A wifi baby camera. Will it be secure?
Armed with $20 and an interest in learninghacking, I visited Canada Computers today to see what ‘extended boxing week sale’ they had. And lo and behold, it was this. A Trendnet WiFi HD Baby Cam TV-IP745SIC. $19. Sweet. Since this is designed to be in your home, monitoring your baby, with bidirectional audio, and cloud…
The Internet of Radon Things
Earlier this week someone brought up Radon gas. He was somewhat surprised that we all knew about it, but we didn’t know enough it turns out. Health Canada has a great resource on it here, including a survey of the prevalence in homes. Radon is the leading cause of lung cancer in non-smokers, and the…
Update on tire repair adventure: Great Success!
OK, earlier I wrote about tire-repairs the way you were never taught in shop class, using spray-foam. The general consensus in the comments was “brilliant idea, terrible execution and outcome!”. Well, naysayers, you are wrong. Today we had a reasonable amount of snow, and I got to try my repair out. And, well, the photo…
The brave new world of car charger virus: my prediction for 2018
The electric car charging cable standard that is going to win is called Combined Charging System. Given Tesla’ scale, they may continue for a while with their proprietary one, but eventually it will phase out somehow. Who wants an appliance that only plugs into its own manufacturer’s power system, can you imagine a GE kettle…