Tag: #tls-wall-of-shame
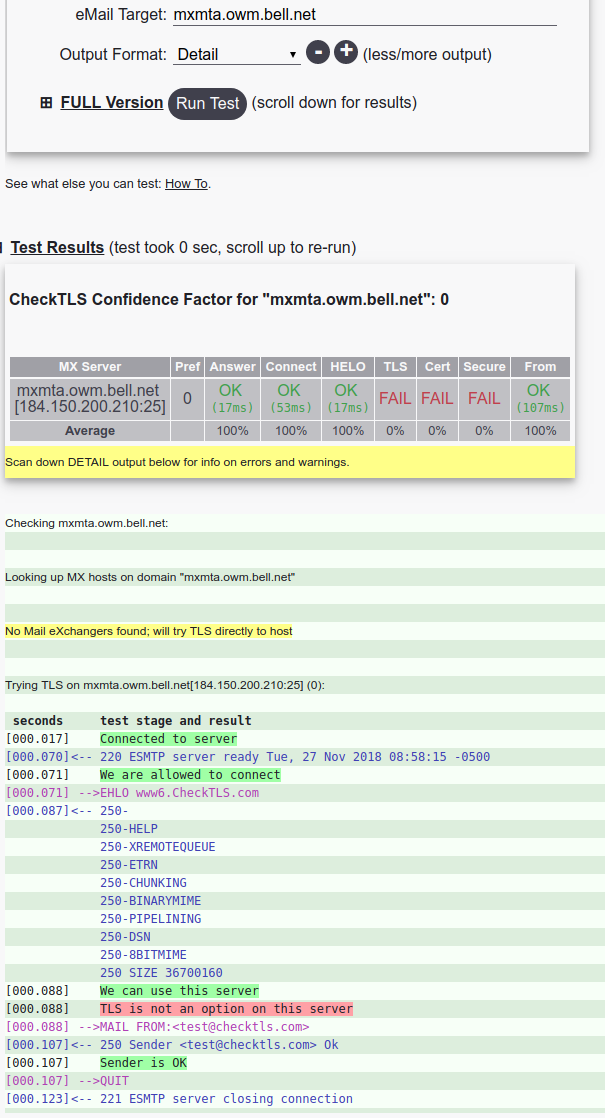
Why does Bell Canada not allow encrypting your email in transit?
Hint: you want your email to be encrypted in transit. Now, lets take a look at some stats. From my earlier post about ‘Why is Canada less encrypted than the US‘?, and from Google’s Transparency Report, we dig into Sympatico. This is Bell Canada‘s brand for Internet. We see that there is no encrypted email exchanged…
Do the phish scammers care more about your security than you do?
Phishing has hit the halfway point on encryption. This means that being TLS-encrypted is no indication a site is real or not (its an indication that it is exactly what it says it is, but not what it might appear as). Ironically, they might be stronger than the average web site. If we look at…
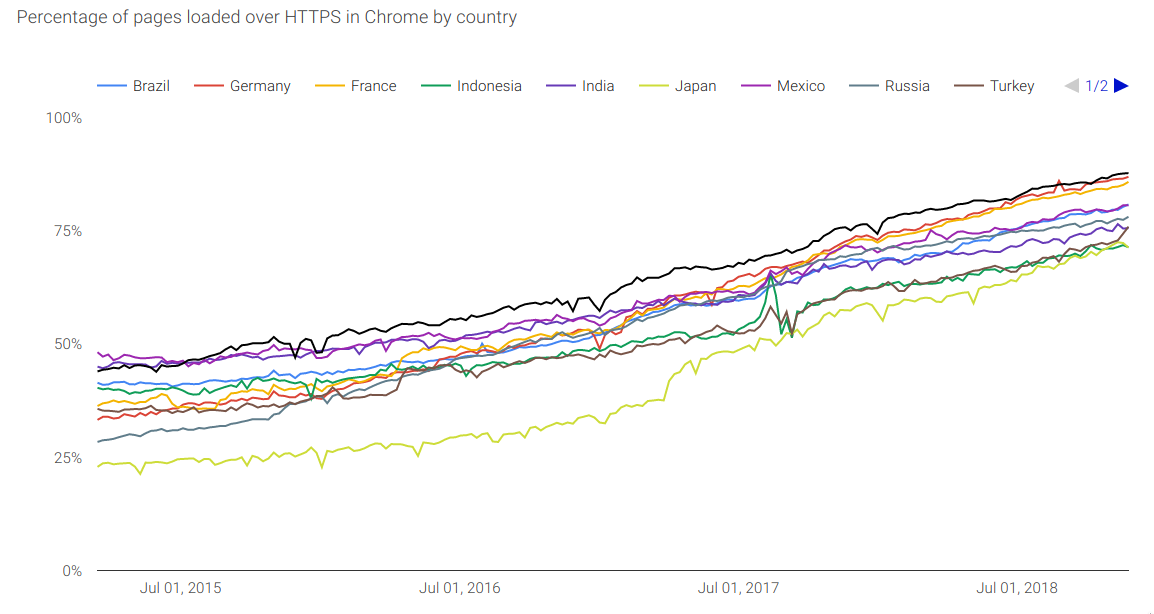
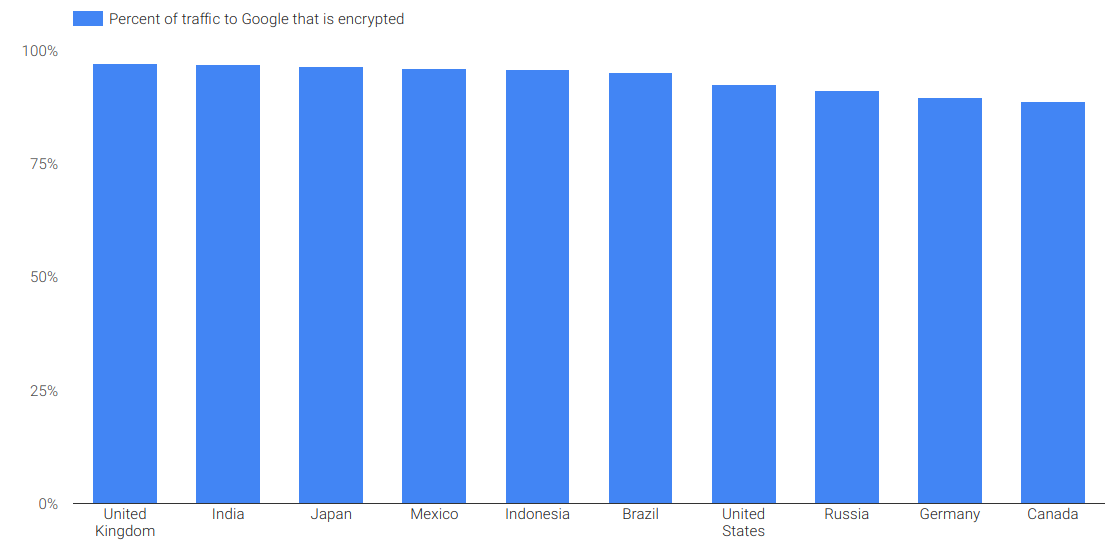
Why is Canada worse than the UK and US for encrypted web?
Courtesy of our friends @ Google and their Transparency Report we see that Canada is 89% encrypted to Google. Good, but not great when you realise the UK is 97% encrypted. What could drive this difference? I would think device-types and ages would be similar. This traffic is a bellwether of other encrypted traffic, and we…
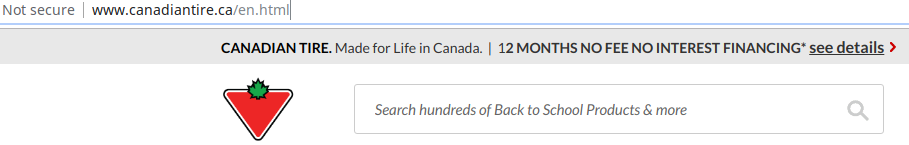
Insecure web sites. #tlswallofshame
You’ve no doubt noticed that chrome now marks any non https-site as insecure. Its no longer that ‘https is secure the rest is unspoken’. Its actively insecure. Some sites have no support for https (shame). Some have support, but you have to remember to use that URL (should redirect). But, what is the thinking behind…