Got a DNS name? (if not, why not?). Make sure the ‘console’ you use to access/control/edit it is locked down with 2-factor authentication. Ideally its e.g. OAUTH2 off your Google account which uses a Yubikey or at least your Android phone for push. Not sure I’d even both with SMS, but I suppose if its that or nothing. I’ll wait, this is important. Its not hard to do, just enable it (and maybe do your Amazon, Github, Gmail while you are at it).
OK, done? Good. You just neutralised half of the horror you are about to read. Now, before I give you the details, while you are in your DNS console, enable DNSSEC, and then check it here. May as well double check your CAA and SPF while you are in there.
OK, back, done? Good. You’ve neutralised most of the rest. So lets read what the good folks at Fireeye have said. Its a method of broadly harvesting all kinds of information by spoofing a machine, without much chance of the victim detecting.
Now, the next step, and my ask of you. For a couple of sites you care about, do a quick check. Do they have DNSSEC enabled? If not, contact them, open a support ticket, give them a tsk tsk sound as you pass them in the hall, whatever you gotta do.
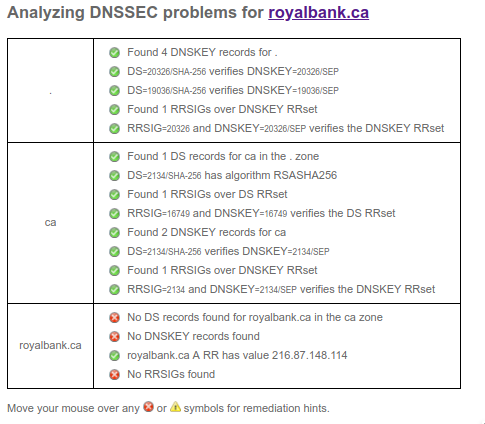
Here's an example, my bank. No DNSSEC. Why not? Lets check the CAA: $ dig -t caa royalbank.com ... NO RECORDS...
This is no good. A CAA record helps prevent you from being spoofed. The above attack, if it can get a hold of your DNS, can sign a certificate w/ Let’s Encrypt. They might not notice the CAA if you have it there.
So, anyone involved with the Royal Bank of Canada want to comment on their DNSSEC practices, why its disabled? Or anyone else want to check your bank and comment here as to whether it has DNSSEC (and CAA)? Takes 1 second to test here.
Its got another bad practice:
http://royalbank.ca redirects to http://www.rbcroyalbank.com. This in turn does not redirect you to the SSL site but serves content, fetches from remote CDNs. You don’t want that. TLS or bust.
$ curl -q www.rbcroyalbank.com |grep https
Leave a Reply