Ever look at a firewall log? For long? Without going blind? Your first reaction is “OMG I’m being hacked”. Who would have the audacity to try and connect to my ssh? After a bit, well, you give up. Its the Internet. There’s a lot of things happening, from research bots, to commercial scanners, to hackers.
Enter greynoise.io. The general idea is that they catalog the ‘low-level noise-floor’ and that you ‘subtract’ it from your logs, leaving the real culprits. Just like in audio processing you would sample a quiet room, and then subtract that from the audio you later record.
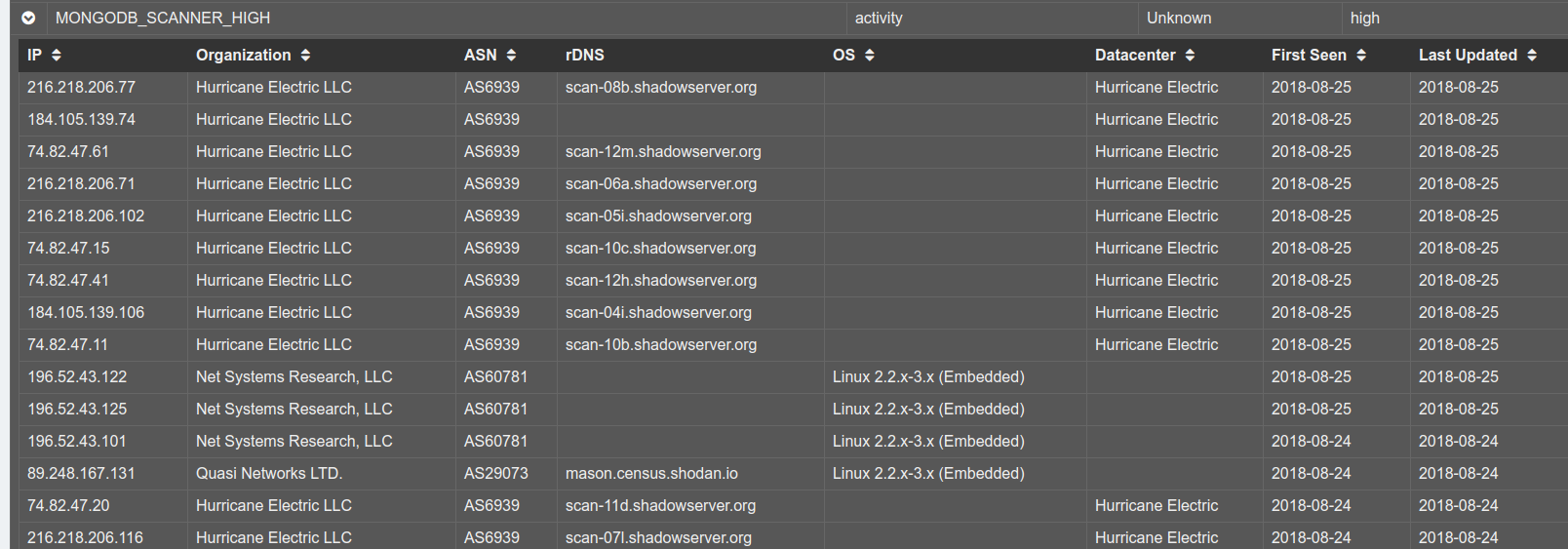
If we look at their ‘visualiser‘, we can see snippets of what they are finding. Here, and example, is showing mongodb scanners. We know from Shodan.io that, yes, people put mongodb on the public Internet. And, if you run it thusly, you will spend a lot of time fishing through logs from Shodan and other tools looking for the real hacker. You’ll spend hours balancing your IDS false-positives, your alerting mechanisms. Educating your SOC. Explaining to your auditors.
Maybe you should just federate your trust of this with greynoise and subtract the crap? There’s an API documented on github for all your data-groping needs.
Leave a Reply