Month: June 2018
My early co-op career comes back again
Today, a pull-request I had made to an upstream software, the maintainer asked me to improve the test coverage, showing the (gcov) coverage report. OK, so as I start working on this, deja-vu comes over me (again). I’ve seen this type of report before. And then it hit me. Many years ago (~1991) I was…
Outdoor cats and air conditioners: just say no
You remember outdoor kitty? The mooch? The one we installed a heated outdoor house and remote temperature sensing for? The same one that is much less friendly when its warm? Well, as we can see, he does not make much use of the house in this weather (~32C here today in sunny waterloo). And no,…
Trust thy neighbour: the windows equivalent of curl | sudo bash
iwr https://chocolatey.org/install.ps1 -UseBasicParsing | iex I find this in the Vagrant file to bring up some Windows docker. Chocolatey? Its a package manager for Windows. The script in question (https://chocolatey.org/install.ps1) is fetched (iwr) and the run (iex). Hmm. Well, if someone gets our DNS, or MITM, we should get an HTTPS alert due to CA…
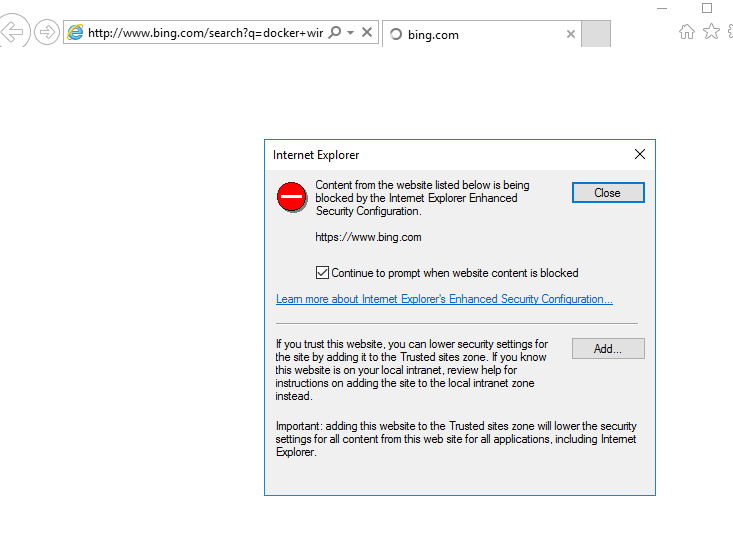
Blocking sketchy sites by default
So yesterday I wrote of my adventures in installing Windows 2016 Server (with Windows Server Containers) into Vagrant. Of course the first think I want to do is try out this ‘docker on windows’ experience. So I open the default browser (edge), and type in ‘docker windows’. And lo, what sketchy site is blocked by…
The bleeding cloud: new exploit based on hyperthread leaking
The ‘snoop thy neighbour’ train continues. Spectre, in the news for most of last year, is a method by which you can snoop on other process memory on the same box. And this in an age of ‘sharing is caring’ where you are running your high-value SSL eCommerce site on the same physical machine that,…