Upstream risks and vulnerability assessment
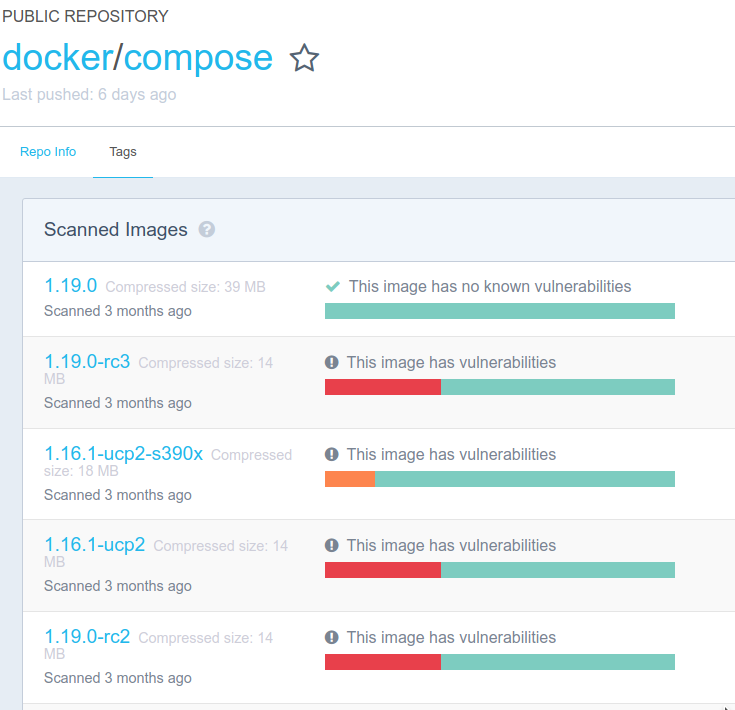
Dockerhub scans some of the images. You can see the results, e.g. docker/compose. Might be interesting to know what the vulnerabilities are I suppose, but, well, less red would be good.
Cloud Lessons: Of gits and ci’s and pipelines and k8s and charts
OK, no cats, no IoT robots, no crappy consumer electronics disassembly, no spray-foam-snowblower tires.. This is a post about the journey to get a source control system + continuous integration system going in a far away cloud. WiFi fireplaces and feral cats will return, I promise 🙂 Also, if you want to make this like…
API keys, clouds, tokens, security
OK, that may be the laziest headline I’ve written in while. Want to be somewhat shocked and appalled? Search ‘mbasanta@vmtestdrive.com’ in Shodan: https://www.shodan.io/search?query=mbasanta%40vmtestdrive.com Helpfully you get the username, password, security tokens to use in the results: And there are a lot of them, all from the same company, all vmware on salesforce for login. Some…
grep using icmpv6 and ptrace?
So in the line of ‘can you trust the upstream’, one of the docker containers I used to do a build causes this to be emitted to the kernel log. And I cannot fathom a legitimate reason grep would be doing either networking or ptrace. [1121294.488937] ICMPv6: process `grep’ is using deprecated sysctl (syscall) net.ipv6.neigh.eth0.base_reachable_time…
The docker reach-around: hacking containers for fun and profit
OK. Those who know me know I use the term ‘hacker’ in the original RFC 1392 sense of the word, “A person who delights in having an intimate understanding of the internal workings of a system, computers and computer networks in particular.”, and not the Hollywood “This is Unix, I know this” where someone can just…

Long Strange Trip