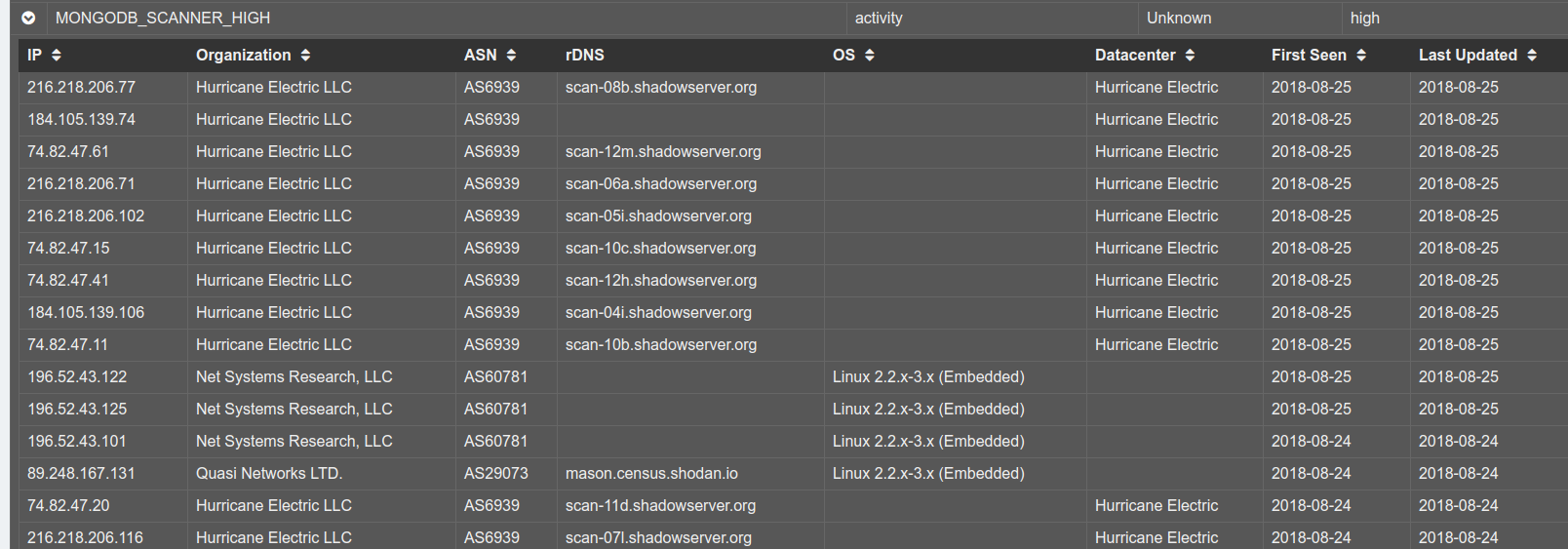
If you don’t stop doing that you’ll go blind: subtract the noise to increase the signal
Ever look at a firewall log? For long? Without going blind? Your first reaction is “OMG I’m being hacked”. Who would have the audacity to try and connect to my ssh? After a bit, well, you give up. Its the Internet. There’s a lot of things happening, from research bots, to commercial scanners, to hackers.…
Tales from the road: the one with the couples massage
Another trip to china, this time escorted (we have a sales person based in HK). We go and do some meetings. Afterwards we go to dinner, he takes me to a mahjong place, we sit in a back room which is isolated and has a bell you ring for service. He explains to me that…
Your cloud firewall is sleeping on the job: the (new) Apache struts vulnerability
In 2016 a vulnerability came to light in Apache struts, a common framework used in Java-based web-apps. In it an attacker could malform a header (really any header) and end up taking over your Java VM. Not so good. E.g. you were one curl away from badness. Well, another struts issue arrived. Same sort of…
T-mobile data breach: it continues to be what you don’t expect
Earlier I wrote about data breaches and the false assurance we are given. In that article, I was warning about personal data and sim-card porting. E.g. someone calls your phoneco, pretends to be you, gets a sim card w/ your number, then calls the bank and pretends to be you forgetting your password and they…
Use vim to open the line from gdb (or gcc err output)
This might be kind of specific. But… We’ve all been there. There’s a backtrace as long as a CVS receipt in your gdb window. mkdir -p ~/.vim/plugin wget -O ~/.vim/plugin/file_line.vim https://raw.githubusercontent.com/bogado/file-line/master/plugin/file_line.vim And now you can: vi source/common/http/http1/conn_pool.cc:79 like a boss. You’re welcome.

Long Strange Trip